Researchers from the University of California recently demonstrated how thermal cameras could theoretically be exploited to steal PIN numbers from unsuspecting victims.
As Sophos security expert Chester Wisniewski notes, thermal imaging provides several advantages. Unlike with traditional cameras, visually masking the PIN pad does not thwart an attack, while the ability to automate PIN harvesting using computer software further simplifies the act.
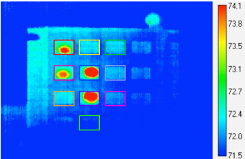
To demonstrate the potential of the above-mentioned attack vector, researchers recruited 21 volunteers and had them test 27 randomly selected PIN numbers using both plastic and brushed metal PIN pads.
As expected, the strength of the participants’ button presses and their body temperature affected the results – to a certain degree.
However, researchers also determined that metal pads made any attack nearly impossible to implement. In contrast, plastic PIN pads allowed the cameras to determine what numbers were being pressed, along with their order.

“With the plastic PIN pad, the custom software the researchers wrote to automate the analysis had approximately an 80% success rate at detecting all digits from a frame 10 seconds after the person entered their PIN,” explained Wisniewski.
“The success rate was still over 60% using a frame 45 seconds after the PIN was entered.”
Although thermal cameras are currently quite expensive, it is likely that thieves could theoretically adopt the technique sometime in the future.
“As far as we know, this attack hasn’t been used in the wild,” he said. ”Nevertheless, the cautious among us could opt to use ATMs with metal PIN pads to reduce the risk of becoming a victim.”






