One of the best yet often unknown cybersecurity solutions is continuous security validation. CISOs, CTOs, and CIOs may be familiar with it, but ordinary business owners and non-tech-savvy CEOs likely are not.
Many organizations are already using penetration testing and red teaming processes, but they may not be providing the best protection. As Enterprise Strategy Group’s senior principal analyst Jon Oltsik explained in a post on CSO Online, these security measures have limitations when it comes to their testing frequency, methodologies, and the highly technical nature of their outputs. Continuous security validation presents an arguably more effective way to address the ever-evolving cyber attacks encountered by most organizations.
Cymulate, a leading security validation platform, offers a simplified process to undertake continuous security validation. This process entails three main steps: the simulation of end-to-end attacks, evaluation, and remediation through actionable insights. Knowing these can be a good starting point for organization leaders to get an idea of how continuous security testing works.
Simulation
The simulation stage consists of a number of sub-stages. These are recon, initial foothold, execution and CnC, network propagation, and the action on objectives. In addition to these standard simulation stages, Cymulate also provides modules to conduct immediate threat analysis, full kill-chain APT, and purple team simulation.
The simulation process starts with reconnaissance, which is the discovery and analysis of external digital assets to determine possible vulnerabilities that can be exploited by attackers. Security professionals can manually collect relevant threat intelligence for this, but with the help of a continuous security testing platform, this can be automated.
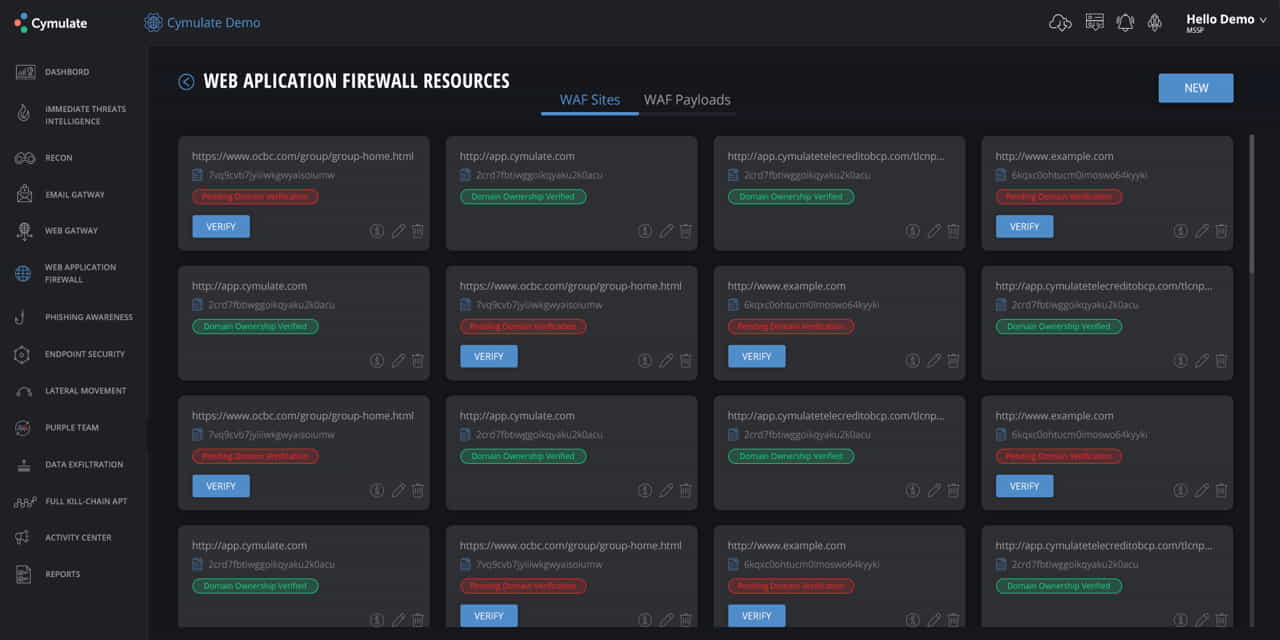
After recon comes the detection of the possible initial foothold of an attack. This means scanning the web gateway, email gateway, web application firewall (WAF), and possible weaknesses that can be penetrated by phishing. Inbound traffic, email attachments, and links are scrutinized to check for possible anomalies. For the WAF, payloads are transmitted to evaluate the behavior of the firewall and ascertain that it works as designed. Phishing awareness, on the other hand, usually involves the generation of custom phishing campaigns to find out how people in an organization respond to such attacks.
After scanning the initial foothold, endpoint security checking follows. This is the main action undertaken during the execution and command and control stage. Its goal is to validate the endpoint security controls and check their efficacy against signature-based attacks, command and control attempts, and ransomware.
After scrutinizing the endpoint defenses, the next step is to simulate the possible network propagation strategies of an attacker. It is in this stage where the lateral movement of an attack is mapped or projected. This stage reveals the potential network vulnerability points, misconfigurations, and network architecture flaws of an organization.
The next stage is to determine action on objectives, and this typically requires data exfiltration or the testing of the effectiveness of the data loss prevention (DLP) system of an organization. Here, simulations are undertaken to check for vulnerabilities in the handling of sensitive or critical data such as payment details, custom regex, and health records.
It becomes easier to simulate attacks when there are tools designed for this, just like what Cymulate offers with its Immediate Threat, Full Kill Chain APT, and Purple Team Simulation modules.
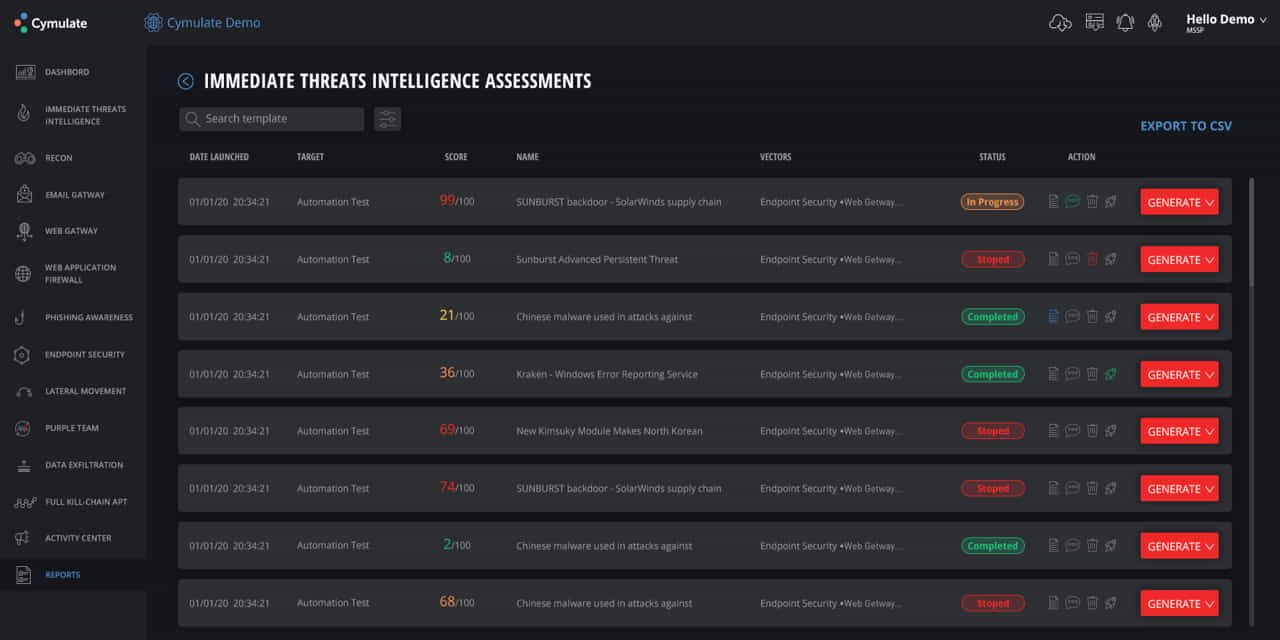
The Immediate Threat module enables quick security posture evaluation in view of the most recent cyber-attacks and threats detected in the wild. It presents a searchable list of recent threats with corresponding urgency scores, statuses, and launch date, and target details.
Meanwhile, the Full Kill-Chain APT module allows organizations to simulate attacks associated with known Advanced Persistent Threat (APT) groups. It can also conduct custom simulations with full kill-chain attack configurations.
Lastly, the Purple Team Simulation module provides an open framework to automate exercises that are normally done manually by red/purple teams. This module specializes in simulating the activities of security assurance programs that are specifically designed for the distinctive environment and security protocols of an organization.
Cymulate’s Purple Team Simulation module is designed to deliver automated security validation and assurance for any kind of organization. It is also created to work in line with the MITRE ATT&CK framework to achieve comprehensive and up-to-date evaluations of security controls.
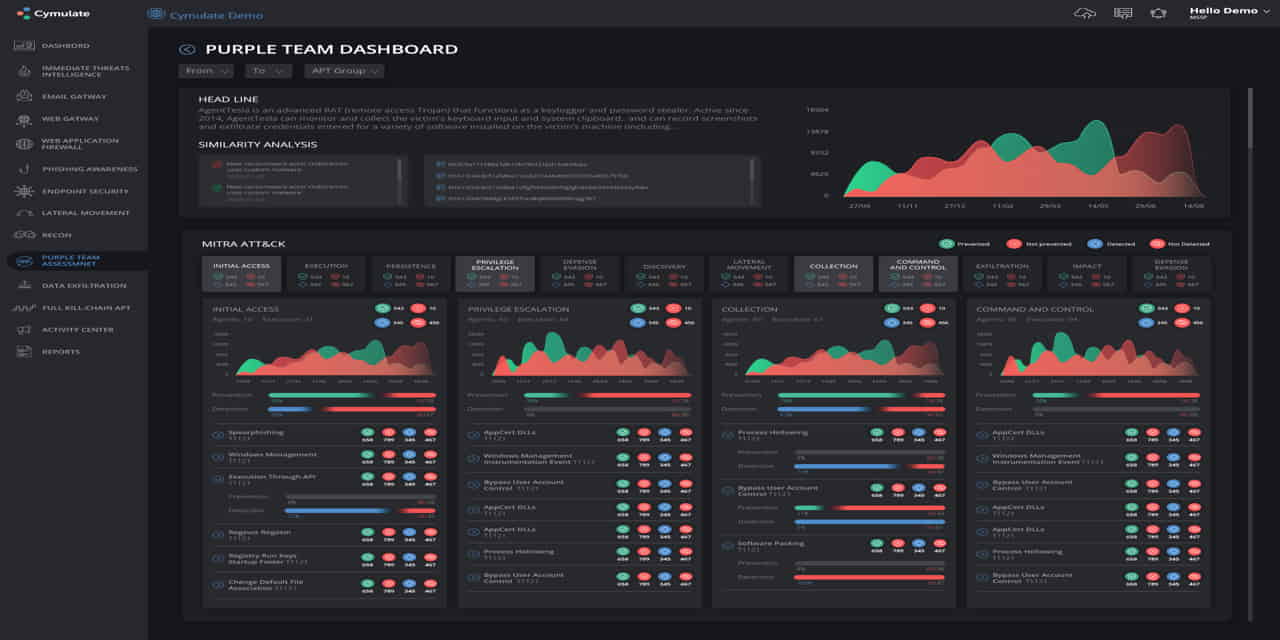
The Purple Team module is notable for its ability to extend automated security visibility and optimization to situations and settings uniquely identified to specific teams, organizations, and personnel. In a way, it is like a bridge to the next stage of the security validation process: security visibility enhancement. Its dashboard includes tools or features that make it easier to monitor security controls and automate recurring evaluations.
Evaluation
Once the simulations are completed, it becomes easier to spot security gaps or weaknesses in an organization. There exists improved security visibility. Consequently, it becomes quicker and more convenient to evaluate weaknesses.
In a manual security validation process, evaluation can be as tedious as the simulations or even more exhausting. Security officers would need to meticulously examine the data produced after the simulated attacks are completed. Fortunately, with the help of automated security validation tools, evaluation can be much quicker and easier to undertake.
Security validation platforms can generate quick comprehensive security reports on the fly. They can also produce scores for different security concerns, so security officers can attend to the most urgent issues as soon as possible.
Cymulate’s security validation platform provides the functions and features necessary to do all of these. It provides the ability to launch out-of-the-box threat intelligence risk assessments designed to be easy to use for security officers of all skill levels. It also enables the fast measurement and monitoring of security performance through tried and tested methods such as Microsoft DREAD, CVSS V3, and NIST.
Remediation
After scrutinizing the results of the simulations and determining which concerns are indeed threats and not just false positives, the logical next step is to implement the reconfigurations, adjustments, replacements, modifications, and other solutions necessary to plug security loopholes and prevent cybercriminals from overcoming an organization’s security controls.
With the help of a reliable security validation platform, the remediation stage should not be a difficult process. Noted platforms like Cymulate readily provide actionable insights designed to seal security gaps effectively and improve the overall security posture significantly.
The different modules mentioned earlier, for example, come with useful information and guides on what to do with the vulnerabilities and weaknesses identified. With the help of an established global security framework like MITRE ATT&CK, the remediation process becomes even more efficient.
In summary
To emphasize, the process described above is about continuous security validation. As such, it does not start with simulation and end with remediation. The process is repeated over and over to continuously protect the security posture of an organization. Simulations are conducted repeatedly in view of new cyber threat intelligence and updates to the MITRE ATT&CK framework. Likewise, evaluations and remediations are undertaken based on the simulations done.
It would be impractical to do all of these manually, so it helps to make use of an automated security validation platform that provides all the necessary functions to conduct simulations easily, evaluate the results comprehensively and proficiently, and remediate the detected problems efficiently.








